Scroll to learn more
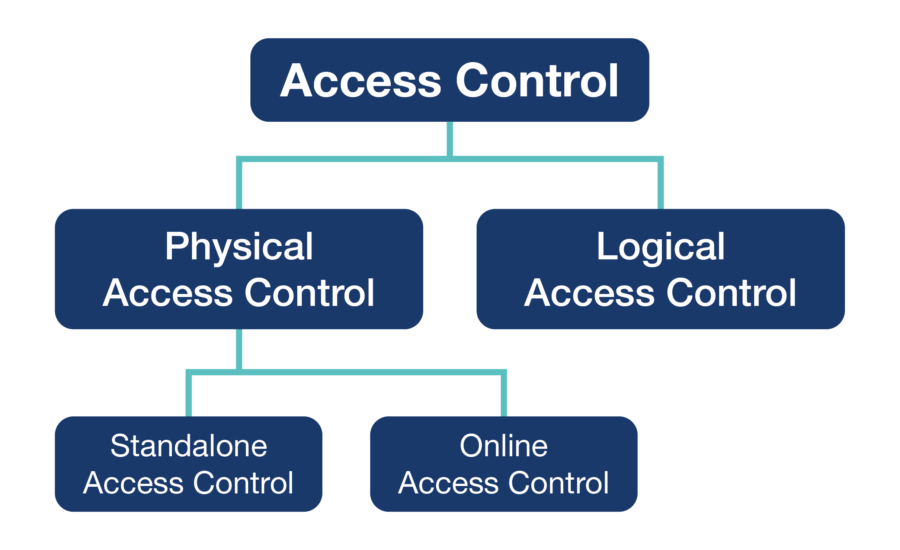
Access control is a security measure that limits who can enter certain areas. Access control can be physical (regulating entry in the built environment with controlled doors, locks, gates, and other barriers) or logical (regulating access to networks, files, or data in a computer system).
Users of an access control system must present credentials that must be verified by the system in order to allow the user to enter. For logical access control systems, the most common type of credential is a password known only to the user. In physical systems, credentials are more varied; it could be a card, a tag, a keypad code, a signal from a smartphone app, or biometric factors such as fingerprints, iris patterns, facial features, or voice tones.
Some systems, both logical and physical, require users to submit more than one credential before they are granted access. This is called multi-factor authentication. For example, in order to log into their office computer, an employee at a company may need to input a password and a randomly-generated access code that is sent to their mobile phone. In a physical access control system, such as in a bank vault, users may need to input a keypad code as well as verifying their identity with a fingerprint reader.
Physical access control (sometimes known as PAC) is utilised in a wide range of building types in every industry. If you have ever:
you have used access control.
While there are a large variety of different kinds of access control systems, they are all comprised of the same essential parts:
Systems can be very simple, controlling entry to just one door or network, or highly complex security ecosystems with multiple layers of access permissions.
For physical access control, there are two principal types of system. Standalone access control (or offline access control) is generally designed for use with smaller premises with a smaller pool of users. The database of users is stored on a reader or keypad installed at the door itself, and each reader or keypad controls just one door. If standalone controls are installed at multiple doors on a site, any addition or removal of users must be repeated at every reader/keypad individually.
Conversely, online access control (also known as networked access control) is better-suited for larger sites with more doors, more users, and more complex entry permission requirements. Online systems store their database of users centrally, either on local computer software or in the cloud via internet connection.
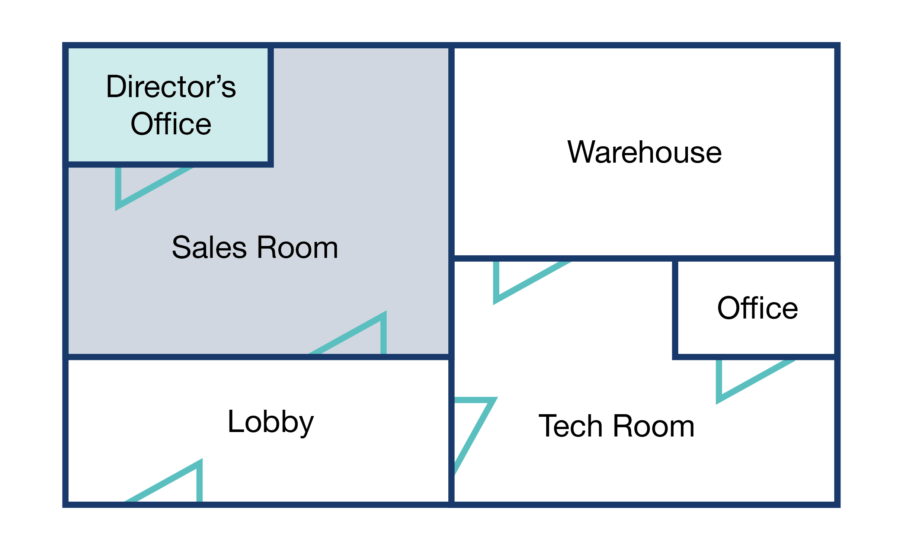
With access control software, individual doors or areas can be managed centrally, mapping out specific sets of access permissions for individual users or groups of users. A layered system like this could mean that every employee can access the front door of the building, but only the Sales team members can access the Sales room, and only the Sales Director can access his private office. Permissions are pre-set and managed centrally on the access control software, so for individuals walking around the building, their movement is smooth and easy.
Security is an essential part of our day-to-day lives. Whether it’s ensuring that only residents can enter an apartment block, only employees can get into the stockroom, or only authorised individuals can access high security facilities, access control is an integral part of our routines.
The basic principle of access control is that only authorised individuals can enter certain restricted areas. If a system is effective, then residents, employees, visitors, or users benefit from the confidence of knowing that nobody can gain entry to areas for which they do not have authorisation.
As well as the obvious protection of people and assets, there are practical benefits to access control, too:
“Pre-COVID, site managers may have managed with a relatively straightforward system. But the benefits of more sophisticated integration are significant, especially when you are managing thousands of users a day.” – IFSEC Global
For sites utilising online access control, integration can help to align your access control system with other building management systems. Bringing CCTV, HR databases, and IT platforms in line with your access control system streamlines administrative processes and significantly reduces bureaucratic loads. If systems aren’t integrated, when an employee starts or leaves a job, they need to be added or removed from every system individually. This is a huge inefficiency that might stretch across multiple departments and leaves a lot of room for human errors.
Better integration also allows for greater flexibility. As the world adapts to the rapidly evolving working patterns enforced by the COVID-19 pandemic, flexibility has become a key distinguishing factor of success.
Organisations offering flexible working hours or a combination of on-site and home working need to be able to accommodate changing traffic patterns. For many businesses, the traditional rush hour influx of people just before 9am and corresponding exodus at 5pm has disappeared.
Access control systems, along with the other systems with which they are integrated, must be flexible enough to accommodate working pattern policies. Many networked access control platforms allow security managers to set schedules that define particular access permissions at particular times for particular people. With much less uniform working patterns becoming the new norm, it’s essential that schedules offer sufficient flexibility to meet an organisation’s changing needs.